Web attack detection using IDPS
A recent webinar organized by C-SAFE on ‘Web Attack Detection Using IDPS: A Robust Approach by Shivam L. Sir to Strengthen Cybersecurity Defenses.'”
Page 1: Cybersecurity Concepts
Tools and Techniques:
Wireshark and VS Code: Used for scripting and network analysis.
SQL: Primary language utilized for database interactions.
Common-client: Used within an Ubuntu environment for certain tasks.
Bypass Techniques:
Encoding:
HTML Encoding in developer mode.
Base64 Encoding.
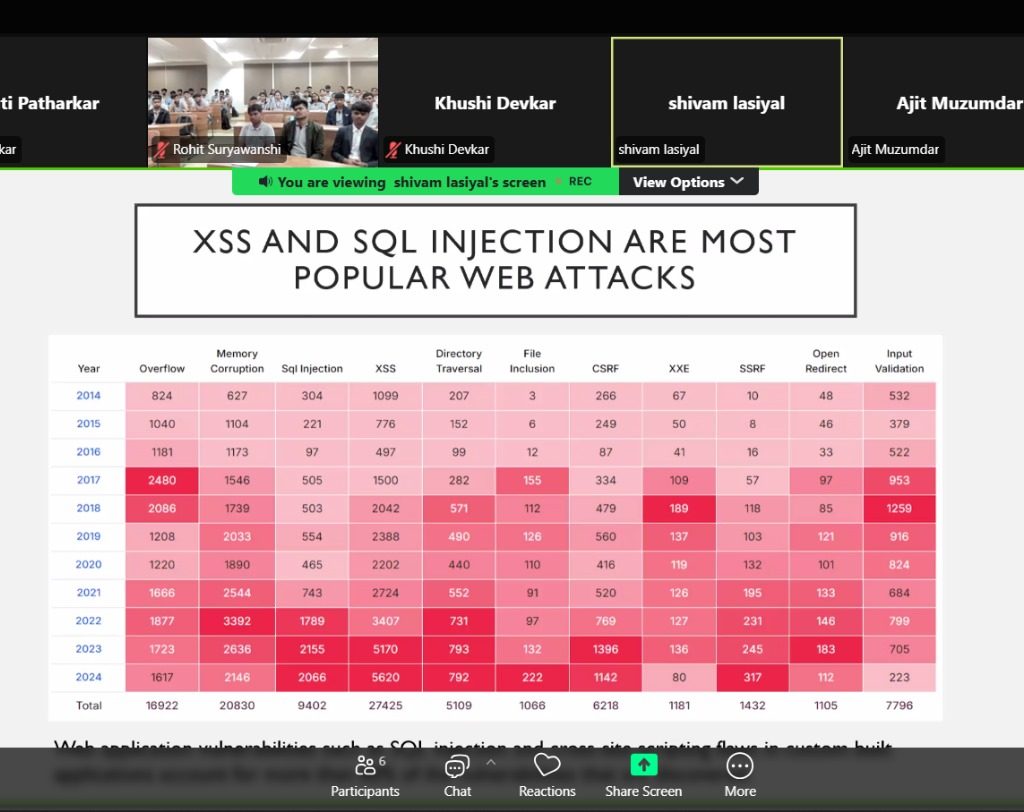
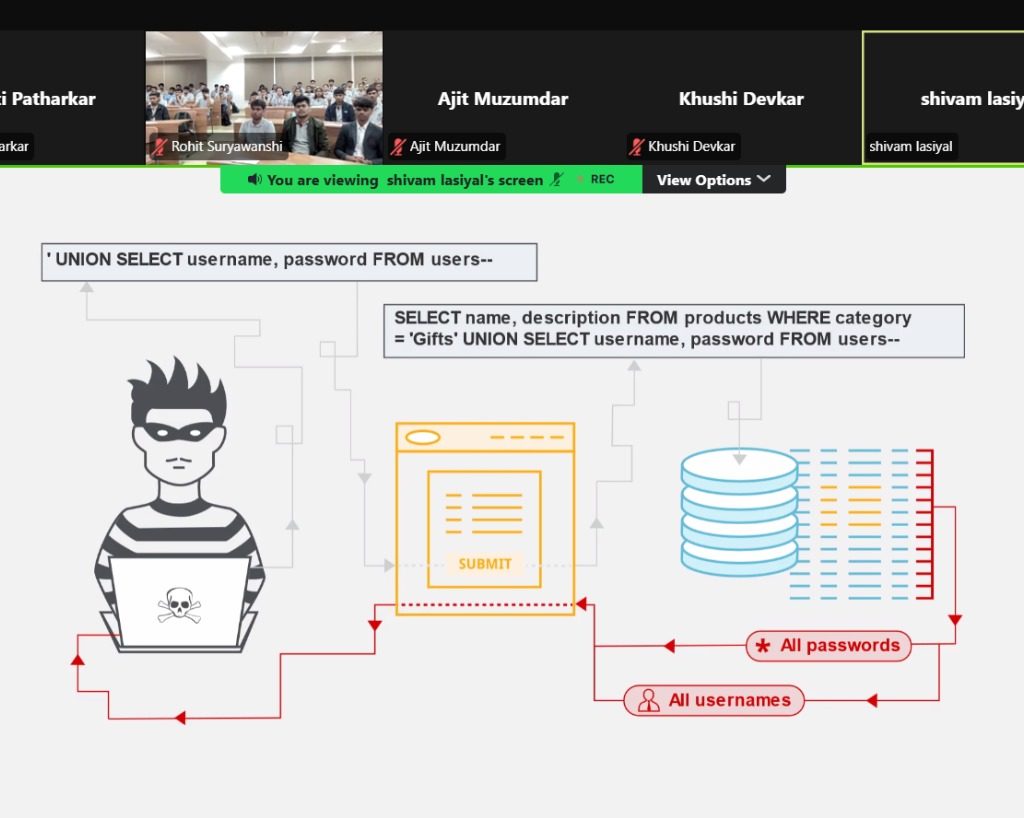
SQL Injection:
Using SQL queries and comments to exploit vulnerabilities.
Converting Base64 to JavaScript for analysis and attacks.
Q&A: Most Harmful Attacks:
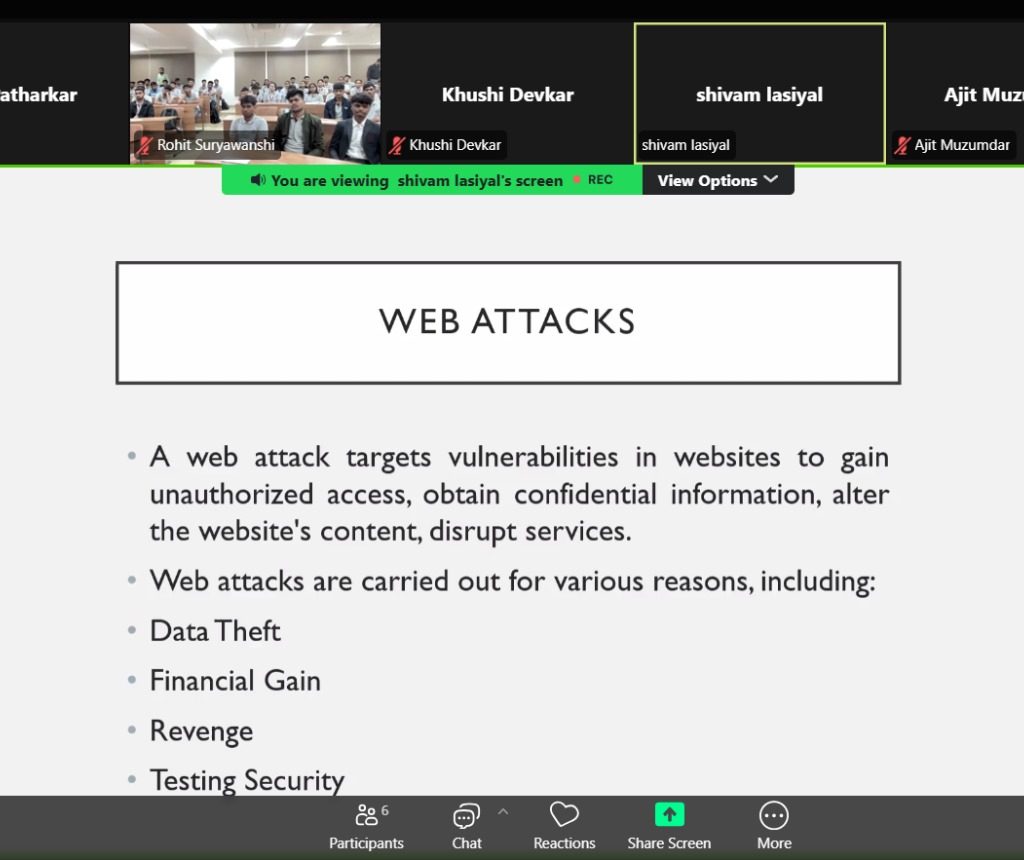
SQL Injection: A severe attack affecting database integrity and security.
Cross-Site Scripting (XSS): Can manipulate entire web applications through
Page 2: Intrusion Detection and Response
Network Analysis Workflow:
Involves several stages:
Packet Decode: Interpreting raw data packets.
Pre-Processor: Initial filtering and preprocessing of data.
Detection Engine: Identifying malicious activity using rules.
Logging: Recording detected threats for further analysis.
Rules are crucial for identifying potential threats in network traffic.
IDS Rule Example:
Example of an Intrusion Detection System (IDS) rule:
plaintext
Copy code
action: alert
protocol: tcp
source IP: any
source port: 23
destination IP: 192.168.12.8
destination port: any
msg: “TCP Packet is detected”
sid: 2000020
Tools:
CyberChef: Used for data encoding, decoding, and manipulation.
Wireshark: For following network streams and deep packet inspection.
regex101.com: A web-based tool for regular expression pattern matching.
Payload exploration using document.cookie to test vulnerabilities.